
Security Breach Information Privacy
Five Nights at Freddy’s: Security Breach is the latest installment of the family-friendly horror games loved by millions of players from all over the globe. Play as Gregory, a young boy trapped overnight in Freddy Fazbear’s Mega Pizzaplex.

Fnaf Security Breach Wallpapers Wallpaper Cave
GuardDuty is part of a broad set of AWS security services that help customers identify potential security risks, so they can respond quickly, freeing security teams to focus on tasks with the highest value. The three new capabilities expand GuardDuty protection to container runtime behavior, as well as database and serverless environments.

I Watched The FNAF Security Breach Gameplay Trailer at 0 25x Speed YouTube
To download and install FNAF: Security Breach for PC, click on the “Get FNAF: Security Breach” button. You will be taken to the product page on the official store (mostly it is an official website of the game). Please, follow next instructions: Press the button and open the official source. It could ask you to register to get the game.

Breach High Resolution Stock Photography and Images Alamy
Descargar Five Nights at Freddy’s: Security Breach [ES] 下载Five Nights at Freddy’s: Security Breach [ZH] Télécharger Five Nights at Freddy’s: Security Breach [FR] Five Nights at Freddy’s: Security Breach herunterladen [DE]

Wallpapers Security Breach Wall Pack FREE DOWNLOAD WinCustomize com
A top administrator with Washington’s health insurance exchange apologized to House members on Wednesday for the data breach that resulted in the disclosure of personal information for thousands of users, including members of Congress. The leak was the result of human error, Mila Kofman, executive director of the District of Columbia Health Benefit Exchange Authority, told a joint session of.

Saturday Morning Security Spotlight Breaches and Intel Cybersecurity Insiders
Download for Windows Softonic review New FNF game installment Five Nights at Freddy’s Security Breach is a survival horror game published by ScottGames. This is the ninth main installment in the Five Nights at Freddy’s series and the thirteenth game overall. The game took place after the events of Five Nights at Freddy’s: Help Wanted.

Cyber Security Incident What to do AM PRO
A security breach occurs when an intruder gains unauthorized access to an organization’s protected systems and data. Cybercriminals or malicious applications bypass security mechanisms to reach restricted areas. A security breach is an early-stage violation that can lead to things like system damage and data loss.

Security Breach 2 in 1 by Aslik VideoHive
Product FNAF: Security Breach download PC is divided into five Nights, each Night gets progressively harder. Players must use their wits and resources to survive a night shift at restaurant. They must carefully monitor animatronics, set up security cameras, use other defensive items to stay alive. Program is full of jump scares and unexpected.
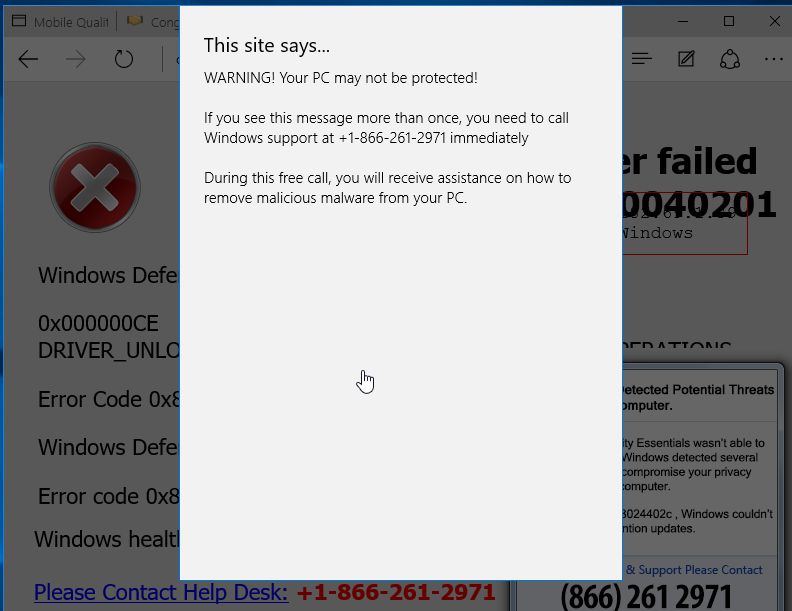
Remove Security breach a in Malware Removal Guide
17 thoughts on ” 3CX Breach Was a Double Supply Chain Compromise ” G.Scott H. April 20, 2023 I cannot speak for all Linux distributions, but on Slackware the techniques described would not.

fnaf security breach download
Twilio, Cloudflare and other organizations reported employees were targeted with a phishing campaign leveraging a kit codenamed 0ktapus. Tune in for this short episode to learn more about the mechanisms behind the phishing campaign and tips for mitigating this threat. To learn more about this breac…
Security breach stock illustration Illustration of digital 34924044
Breach and attack simulation platforms have evolved to deliver more advanced attack simulation capabilities.. Read the latest discovery report from S&P Global Market Intelligence for insights about the continuous security validation methods modern security organizations are using to more effectively validate their security posture. Download.

Security Breach poster fivenightsatfreddys
Go to your download folder and open the APK file with Bluestacks to install the app in the emulator. Wait for the installation to complete. Alternatively, you can click on the Install APK button within the emulator, select the APK from your downloads, and wait for the app to successfully install.
Computer Security Breach Stock Photo Download Image Now iStock
You can play by downloading it from the official website or by purchasing it from a retailer. Once you have downloaded it, you will need to unzip the file and then double-click on the “SecurityBreach.exe” file to launch. What are the system requirements? This requires a PC with Windows 7 or higher.

Security breach symbolism Digital binary code on computer screen pen pointing out security
ICICI Bank denies data breach allegation (Image source: REUTERS/Francis Mascarenhas) On 21 April, CyberNews published a report saying over 3.6 million ICICI Bank files comprising the bank’s and its clients’ information was leaked from a publicly accessible cloud storage bucket managed by DigitalOcean, a New York-based cloud service provider. The purported data leak, according to the research.

The 8 Biggest Security Breaches in History
The breach involved names, personal information, and Social Security numbers. Individual notifications state the exact types of information that were exposed/acquired. Identity theft protection services have been offered to affected individuals and security practices have been reviewed and enhanced and additional training has been provided to.

What is a security breach and how to avoid one
Define Security breach. Security breach synonyms, Security breach pronunciation, Security breach translation, English dictionary definition of Security breach. The protection resulting from all measures to deny unauthorized access and exploitation of friendly computer systems.
